
Cloud Network Security is a paramount aspect of this evolving technological landscape. As more sensitive information and mission-critical functions migrate to the cloud, safeguarding these digital assets from an ever-growing array of cyber threats becomes imperative.
In this era, network security extends beyond traditional perimeters, necessitating innovative approaches to protect cloud environments and data.
We will examine the unique security considerations presented by cloud networks, the threats that loom in this environment, and the advanced solutions designed to fortify your organization’s digital presence in the cloud.
What exactly is cloud network security?
Cloud Network Security is a crucial aspect of cloud computing that helps protect public, private, and hybrid cloud networks from unauthorized access, modification, misuse, or exposure. It is one of the foundational layers of cloud security that enables companies to embed security monitoring, threat prevention, and network security controls to help manage the risks of the dissolving network perimeter.
If you expand your current network to cloud-based environments, there are a variety of consequences for security. Historically, every on-premises solution had an undefined perimeter between your internet and the internal network, as well as several multi-layered security measures like physical firewalls and routers, intrusion detection, and much more. However, as more users and workloads move over the on-prem boundary, it becomes more challenging to recognize and react to attacks using the previous security measures to create an effective network.
To keep pace with the rapid growth of today’s IT environments, companies require a more straightforward method to deploy and manage network security that is integrated directly into the cloud. Cloud-based security for networks allows you to reduce risks, meet the requirements of compliance, and guarantee secure and efficient operations.
According to Google Cloud, cloud network security refers to the security measures–technology, policies, controls, and processes–used to protect public, private, and hybrid cloud networks. As with cloud security, security is a term that refers to the policies, technology control, procedures, and methods employed to safeguard data. It only focuses on protecting cloud networks from unauthorized access and misuse or exposure. Cloud security is one of the primary layers of cloud security, which allows companies to incorporate surveillance of security, threat detection, and security measures for networks to manage the security risks associated with the disappearing firewall.
Why is cloud network security important?
Cloud network security is essential because it helps protect public, private, and hybrid cloud networks from unauthorized access, modification, misuse, or exposure. When you connect your existing network to cloud-based environments, it comes with numerous security implications. Historically, any on-premise approach involved a distinct perimeter between the internet and your organization’s internal network and a variety of multi-layered defences like physical firewalls, routers, intrusion detection, and more. But as more workloads and users move beyond your on-premise perimeter, it becomes harder to detect and respond to intrusions using previous perimeter protections to create a secure network.
Utilizing cloud network security is necessary when using cloud-based infrastructure to safeguard your systems, data, and apps. With cloud network security, you can guarantee secure and effective operations, reduce risk, and comply with regulations. Utilizing cloud-based infrastructure that incorporates network security features like policy-based enforcement mechanisms and centralized monitoring helps minimize risk and ensure secure operations for enterprises.
In summary, cloud network security is an essential aspect of cloud computing that helps protect public, private, and hybrid cloud networks from unauthorized access or exposure. It forms one of the foundational layers of cloud security that enables companies to embed security monitoring, threat prevention, and network security controls to help manage the risks of the dissolving network perimeter.
How is it different from traditional network security?
Cloud network security and traditional network security are different in several ways.
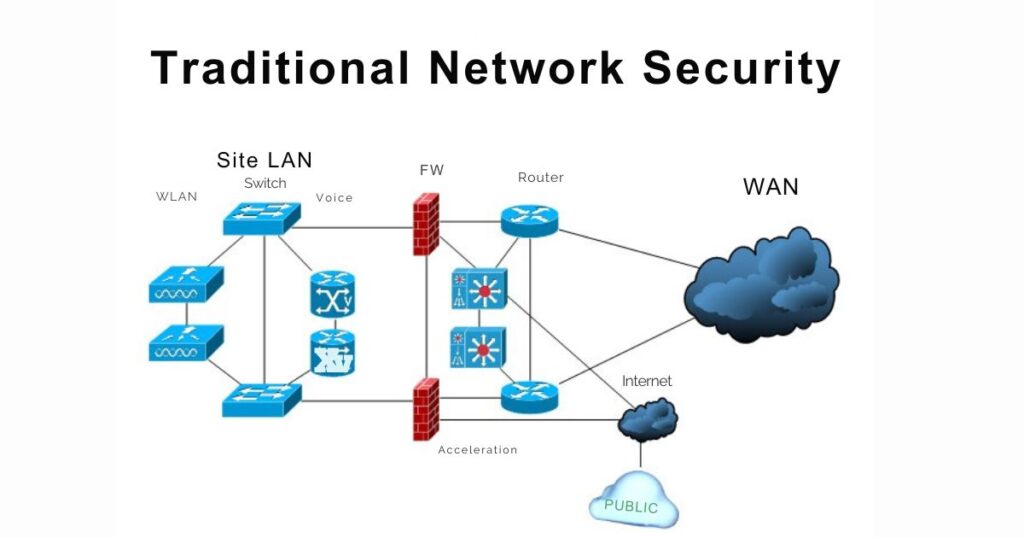
Traditional network security involves securing the underlying infrastructure that supports computing, such as routers, switches, firewalls, and other devices. It also includes ensuring the communication channels between different components of a computing infrastructure.
On the other hand, cloud network security describes the technologies, procedures, controls, and policies that are utilized to safeguard public, private, and hybrid cloud networks. Similar to cloud security, cloud network security is the exclusive focus of safeguarding cloud networks against unauthorized access, modification, misuse, or disclosure. It encompasses the technology, rules, controls, and procedures used to protect data. One of the fundamental pillars of cloud security is cloud network security, which enables businesses to incorporate threat prevention, security monitoring, and network security controls to help limit the risks associated with the network perimeter collapsing.
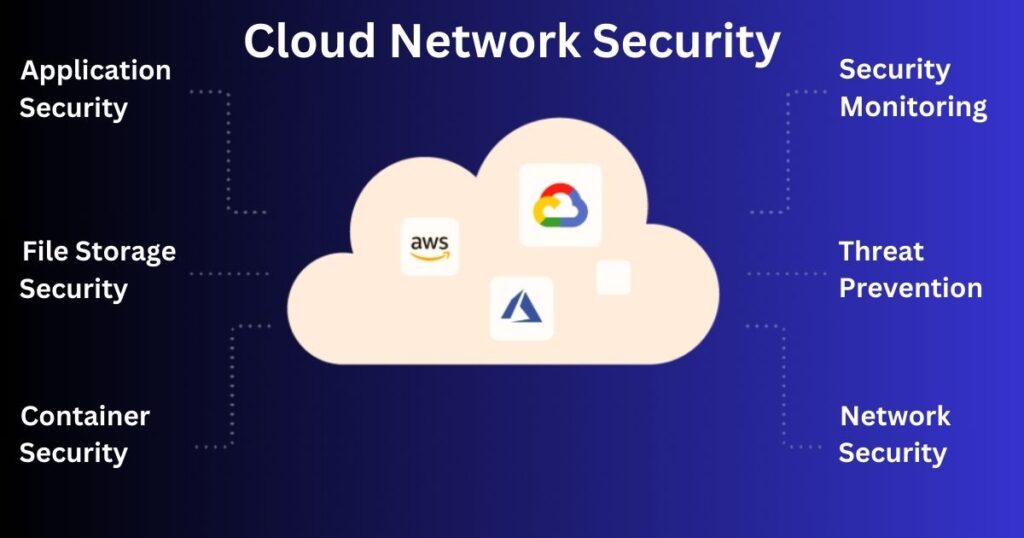
One of the key differences between traditional network security and cloud network security is that traditional network security is primarily focused on securing on-premises infrastructure. In contrast, cloud network security is focused on securing cloud-based infrastructure.
Another difference is that traditional network security typically involves deploying physical devices such as firewalls and intrusion detection systems. In contrast, cloud network security relies on virtualized solutions that are built directly into the cloud environment.
In summary, while both traditional network security and cloud network security are essential aspects of securing computing infrastructure, they differ in their focus and approach. Traditional network security focuses on securing on-premises infrastructure, while cloud network security focuses on securing cloud-based infrastructure using virtualized solutions.
Threats to Cloud Network Security
Cloud networks are vulnerable to various types of threats, such as data breaches, malware attacks, DDoS attacks, insider threats, and more. These threats can cause significant damage to your business by compromising sensitive data or disrupting critical services. Therefore, it is essential to understand these threats and take appropriate measures to mitigate them.
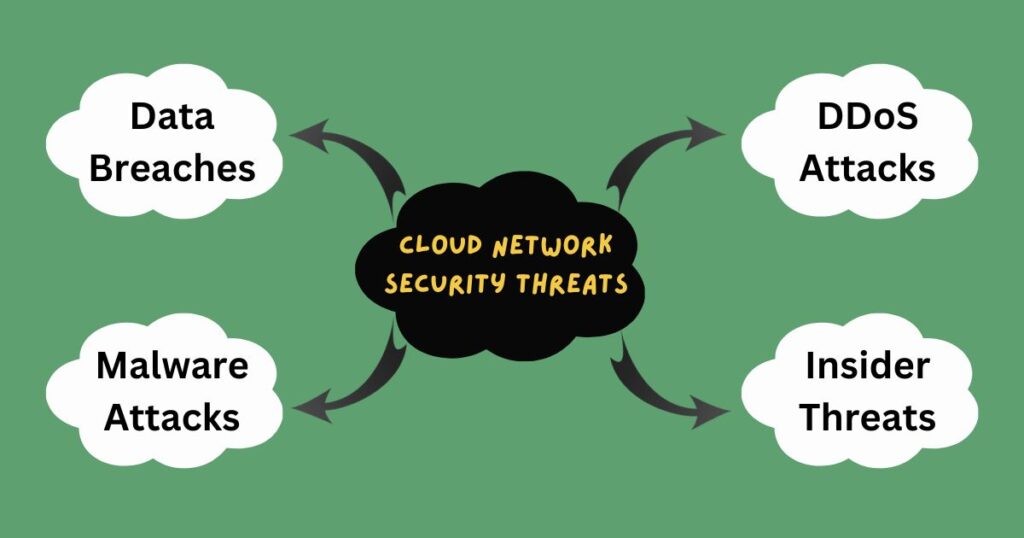
Some common threats to cloud network security include:
- Data Breaches: Unauthorized access or theft of sensitive data can lead to significant financial and reputational damage to an organization. Data breaches can occur due to various reasons, such as weak passwords, unpatched software vulnerabilities, or social engineering attacks. Attackers can use stolen data for identity theft, financial fraud, or other malicious purposes.
- Malware Attacks: Malicious software that can infect your systems and steal data or disrupt services. Malware can enter your plans through various means, such as email attachments, malicious websites, or infected software. Once inside your systems, malware can steal sensitive data, encrypt files for ransom, or cause system crashes.
- DDoS Attacks: Distributed Denial-of-Service attacks that can overwhelm your systems with traffic and cause them to crash. DDoS attacks are often used to disrupt the availability of online services or extort money from organizations. Attackers can use botnets or other means to generate massive amounts of traffic that can saturate your network bandwidth and make your services unavailable.
- Insider Threats: Malicious or negligent insiders who can intentionally or unintentionally cause harm to your systems. Insider threats can come from employees, contractors, or partners who have authorized access to your plans and data. They can steal sensitive data, introduce malware, or cause system outages due to negligence or mistakes.
Cloud Network Security Solutions
There are several solutions available for securing cloud networks. Here are some best practices for implementing cloud network security solutions:
- Encryption: Encrypting data at rest and in transit can help protect it from unauthorized access. Encryption should be implemented using robust encryption algorithms and keys, and the keys should be managed securely. It is also vital to ensure that the encryption solution is compatible with your cloud environment.
- Access control: Implementing strict access control policies can help prevent unauthorized access to your systems. Access control policies should be based on the principle of least privilege, which means that users should only have access to the resources they need to perform their job functions. Access control policies should also be regularly reviewed and updated to ensure that they are effective.
- Firewalls: Deploying firewalls can help monitor incoming and outgoing traffic and block malicious traffic. Firewalls should be configured to allow only authorized traffic and should be regularly updated with the latest security patches.
- Intrusion detection/prevention systems: Deploying intrusion detection/prevention systems can help detect and prevent malicious activity on your plans. These systems use various techniques, such as signature-based detection, anomaly detection, and behavioural analysis, to identify potential threats. They should be configured to generate alerts when suspicious activity is detected, and the warnings should be reviewed promptly.
- Security information and event management (SIEM): Implementing SIEM solutions can help monitor your systems for suspicious activity. SIEM solutions collect and analyze log data from various sources to identify potential security threats. They can also generate alerts when suspicious activity is detected, enabling security teams to respond quickly.
It is important to note that there is no one-size-fits-all solution for securing cloud networks. The best approach depends on your specific business needs and requirements. By following these best practices, you can minimize the risk of cloud network security breaches.
In conclusion, network security is a critical aspect of cloud computing that cannot be ignored. Securing cloud networks requires a multi-layered approach that involves implementing various technologies, policies, controls, and processes. By following best practices for securing cloud networks, such as encryption, access control, firewalls, intrusion detection and prevention systems, and SIEM solutions, you can minimize risk and ensure safe and efficient operations in your organization’s cloud environment.

Leave a Reply
You must be logged in to post a comment.