
Quantum cryptography is a new and exciting field of cryptography that uses the principles of quantum mechanics to create unbreakable codes. It is based on the fact that quantum information cannot be copied or measured without disturbing it. This makes quantum cryptography extremely secure, as any attempt to eavesdrop on a quantum communication channel will be immediately detected.
In this article, we will explore the world of quantum cryptography and discuss its potential to change the way we live and work. We will also discuss the challenges that need to be overcome before quantum cryptography can be widely deployed.
What is Quantum Cryptography?
The process of encrypting data, or turning plain text into jumbled information that can only be read by someone with the appropriate “key,” is known as cryptography, and quantum cryptography is a realm where the arcane dance of particles embraces the essence of encrypting information and delves into the labyrinth of quantum mechanics.
Quantum cryptography uses quantum mechanics laws and principles to secure data encryption. It uses unique properties like superposition and entanglement to transmit data in an uncrackable way. Quantum states of particles like photons are detectable, allowing for the communication of encryption keys or data that cannot be hacked without leaving evidence of tampering.
Behind the veneer of simplicity in definition, the intricate tapestry of quantum cryptography unravels through the lens of quantum mechanics, entailing nuances such as:
- The inherent uncertainty of particles constituting the universe makes them capable of simultaneous existence in multiple locations or states.
- Photons, the elemental carriers, are spontaneously generated in one of two quantum states, an act of randomness inherent in their quantum nature.
- The paradox that attempting to measure a quantum property inevitably alters or disturbs it, is a fundamental tenet challenging conventional notions of observation.
- The partial duplicability of some quantum properties of a particle, while the entirety of the particle remains beyond the reach of replication.
In essence, quantum cryptography operates on the enigmatic principles of quantum mechanics, where the very fabric of the universe converges with the quest for secure and untamperable data transmission.
Foundations of Quantum Mechanics
To understand quantum cryptography, one must delve into the mysterious realm of quantum mechanics. This science describes the fundamental behaviour of matter and energy at the atomic and subatomic levels. Unlike classical mechanics, quantum mechanics is based on the idea that physical systems can exist in a superposition of states, meaning that they can be in multiple states at the same time.
One of the most important concepts in quantum mechanics is entanglement. Entanglement is a phenomenon where two or more quantum systems are linked together in such a way that they share the same fate, even if they are separated by a large distance. If a measurement is performed on one entangled system, the outcome of that measurement will instantly and irrevocably affect the other entangled systems.
Quantum superposition and entanglement are two of the key principles that underlie quantum cryptography. Quantum cryptography uses the unique properties of quantum systems to create codes that are unbreakable using classical methods.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) is a promising application of quantum cryptography, utilising the quantum properties of particles to create a secure communication key. Encoded on quantum particles like photons, QKD ensures that any attempts to measure or intercept the particles collapse their quantum state, alerting parties of the breach. This unique ability makes QKD essential for protecting communication and potentially the only robust means for distributing secure encryption keys.
Benefits of Quantum Cryptography
Quantum cryptography offers a number of benefits over traditional cryptography, including:
- Unbreakable security: Quantum cryptography is based on the principles of quantum mechanics, which are very difficult to break.
- Long-distance communication: Quantum cryptography can be used to create secure communication channels over long distances, even if the communication channel is not physically secure.
- Resistance to eavesdropping: Quantum cryptography is resistant to eavesdropping because any attempt to eavesdrop on a quantum communication channel will be immediately detected.
Challenges of Quantum Cryptography
Despite its many benefits, quantum cryptography also faces a number of challenges, including:
- Cost: Quantum cryptography systems are currently very expensive to build and operate.
- Complexity: Quantum cryptography systems are complex and require specialized expertise to operate and maintain.
- Distance limitations: Quantum cryptography systems are currently limited to short distances, although research is ongoing to extend the range of quantum communication channels.
How does Quantum Cryptography Work?
Quantum cryptography is a revolutionary new way to secure communication. It uses the principles of quantum mechanics to create a secret key that is unbreakable by even the most powerful computers.
The key to quantum cryptography is the use of photons, or particles of light. Photons can be in one of two polarisation states: vertical or horizontal. These states can be used to represent bits, with vertical representing 1 and horizontal representing 0.
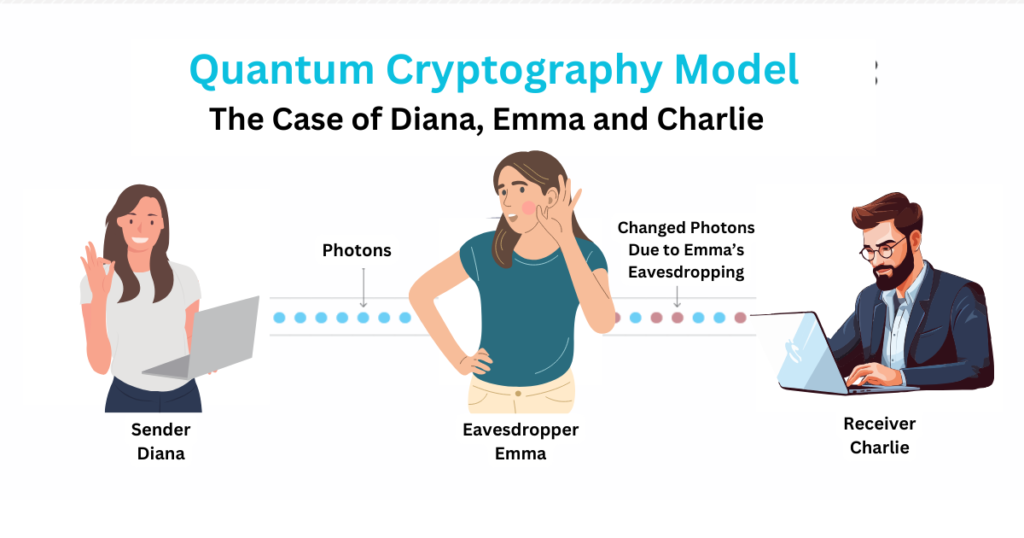
To generate a secret key, suppose, Charlie and Diana, the two parties who want to communicate securely, exchange a series of photons. Each photon is randomly polarised in one of the two states. If an eavesdropper, Emma, tries to intercept any of the photons, she will inevitably disturb their polarisation. This disturbance will be detected by Charlie and Diana, and they will know that their communication has been compromised.
Once Charlie and Diana have exchanged the photons, they compare notes to determine their polarisation states. Any photons that were disturbed by Emma are discarded, and the remaining photons form the secret key. This key can then be used to encrypt and decrypt messages, ensuring that their communication is secure.
One of the unique aspects of quantum cryptography is that it relies on the fundamental properties of quantum mechanics, which are very difficult to break. Even if Emma has unlimited computational power, she will not be able to crack the secret key without being detected.
Another unique aspect of quantum cryptography is that it can be used to create a truly random key. This is important because traditional encryption algorithms rely on keys that are not truly random. If an attacker can guess the key, they can decrypt the message. However, with quantum cryptography, the key is generated using the random polarisation states of photons, which is impossible to predict.
Quantum cryptography is still in its early stages of development, but it has the potential to revolutionise the way we communicate. By using the principles of quantum mechanics, quantum cryptography can create a level of security that is unbreakable by even the most sophisticated adversaries.
Here is a unique analogy to help understand how quantum cryptography works:
Imagine that Charlie and Diana are two secret agents who need to exchange a secret message. They have a special device that can generate a pair of quantum-entangled coins. These coins are linked together in such a way that if you flip one coin, the other coin will instantly flip to the same state, even if it is miles away.
Charlie and Diana each take one of the coins and go to separate locations. Charlie then flips his coin. This instantly causes Diana’s coin to flip to the same state. Charlie and Diana can then communicate securely by revealing the state of their coins. If Emma, the eavesdropper, tries to intercept the coins, she will inevitably disturb the entanglement between them. This disturbance will be detected by Charlie and Diana, and they will know that their communication has been compromised.
Quantum cryptography is similar in that it uses the unique properties of quantum mechanics to create a secure communication channel. If an eavesdropper tries to intercept the communication, they will inevitably disturb the quantum state of the information, and the sender and receiver will know that their communication has been compromised.
Quantum Cryptography vs Traditional Cryptography
Here is an expanded and rewritten version of the text with additional information on cryptography:
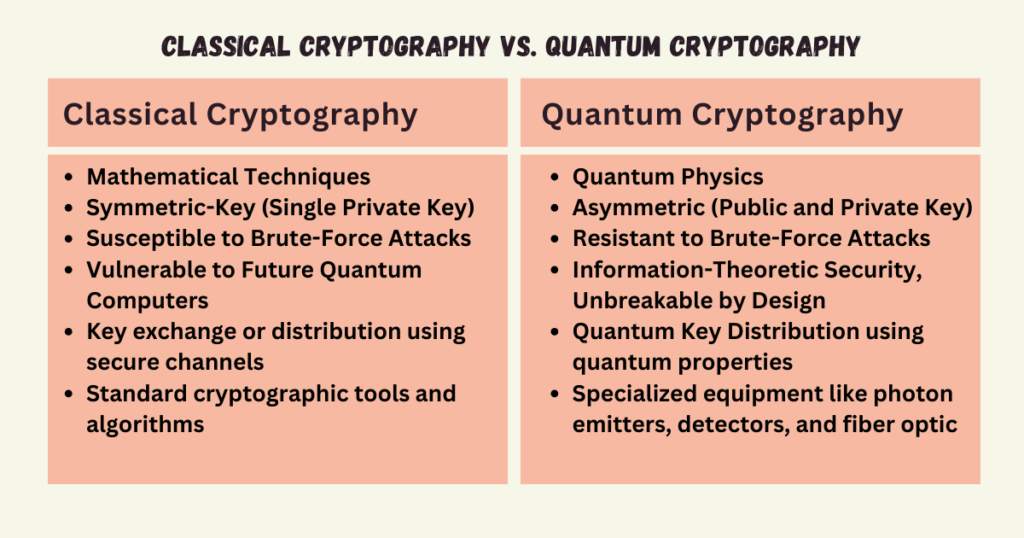
Traditional cryptography relies on mathematical techniques to encrypt and decrypt data. Symmetric-key cryptography uses a single private key for both encryption and decryption. Asymmetric or public-key cryptography uses paired public and private keys; data encrypted with the public key can only be decrypted by the private key. These methods enable secure communication by scrambling data mathematically.
However, traditional cryptography is potentially vulnerable to brute-force attacks as computing power grows. Quantum computers could one day crack mathematical encryption methods by quickly factoring the large numbers comprising cryptographic keys.
Quantum cryptography offers a solution by leveraging quantum physics rather than math for encryption. It takes advantage of quantum properties like superposition, entanglement, and uncertainty to ensure secure communication. For example, quantum key distribution uses photon polarisation to distribute encryption keys that cannot be intercepted without detection.
While traditional cryptography is computational, quantum cryptography is physical; it exploits the fundamental rules of physics to protect data. Measuring a quantum system inevitably alters it, immediately revealing any eavesdropping. This creates unbreakable information-theoretic security.
Quantum cryptography is a nascent field requiring specialised equipment like photon emitters and detectors and fibre optic channels. Ongoing research aims to make quantum cryptography more practical for real-world deployment. But it promises perfectly secure communication that is resistant even to future quantum computers.
Quantum Cryptography for Everyday Users
While quantum cryptography may seem like a technology reserved for high-stakes scenarios, there is potential for its integration into everyday consumer technology. This has profound implications for personal online security, offering individuals a level of protection previously thought to be unattainable.
While traditional encryption remains secure against modern attacks, quantum cryptography offers long-term protection in an era of exponentially advancing computing power. Current cryptographic techniques rely on mathematical complexity that will become hackable by quantum computers. Quantum encryption’s physics-based security can withstand even quantum computational brute force.
The future of quantum cryptography
Quantum cryptography, though still maturing, is a revolutionary advancement with profound implications. By exploiting quantum mechanical properties, it provides mathematically unbreakable encryption secured by the laws of physics themselves. Even intercepting keys collapses delicate quantum states, alerting both parties. This unprecedented technical feat neutralises future computational threats.
Ongoing research strives to overcome implementation hurdles and make quantum encryption robust and user-friendly enough for widespread adoption. But its core concepts offer perfect, physics-based security that current encryption lacks. Quantum techniques will likely become essential in the coming decades as computing continues to rapidly advance.
Real-world quantum encryption may take years or longer to refine. However, its theoretical foundations are already unmatched in ensuring future-proof, hack-proof data transmission. Quantum cryptography’s development epitomises perseverant scientific ingenuity in overcoming once-impossible challenges. Its innovations bring humanity closer to achieving the ancient dream of perfectly secure communication.
Conclusion
In conclusion, the fascinating world of quantum cryptography opens up new frontiers in the quest for unbreakable security. From the principles of quantum mechanics to real-world applications, the journey into this cutting-edge field is both thrilling and promising. As we navigate the challenges and harness the potential of quantum cryptography, a future of secure and private communication awaits.
Leave a Reply
You must be logged in to post a comment.